Disable PHP execution for better WordPress security
Bulletproof Backups for Your WordPress Website
Fortify your business continuity with foolproof WordPress backups. No data loss, no downtime — just secure, seamless operation.
Certain folders in WordPress, like uploads, are writeable by default so that users can upload files (images, videos, etc) onto your site. Themes and plugins also create files in their respective cache directories while at work which isn’t possible unless these directories are writeable. However, this also opens up your site for potential attacks. Hackers can exploit these writeable directories by uploading malicious PHP code onto them and executing them remotely to wreak havoc on your site. The mailpoet hack, for example, allowed attackers to upload malicious scripts to the uploads folder that let them do anything with your site.
We cant do away with the write permissions that prevents uploads to these directories. But what we can do is to reduce the scope of the attacks by removing execute permissions on them. One of the simplest ways to disable PHP execution in certain folders is by adding the following lines to the htaccess file –
<FilesMatch “\.(php|php\.)$”>
Order Allow,Deny
Deny from all
</FilesMatch>
The 1st line ensures that any filename having php in it is caught. So even if the hacker uses something like hackerPHPFileDisguisedAsAJPGFile.php.jpg, it will still be prevented from execution.
For maximum security, create an htaccess file with the four lines of code specified above in the following folders in your WordPress installation:
- /wp-content/uploads
- cache folders within themes and plugins
Even if an attacker gets his PHP code into these directories, he will definitely not be able to execute it.
Tags:
Share it:
You may also like
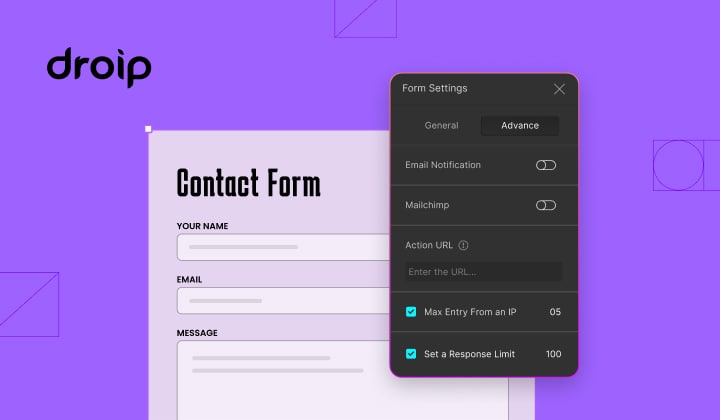
How to Limit Form Submissions with Droip in WordPress
Forms are an indispensable part of any website because of their versatility, letting you collect information for various purposes! However, people with ill intentions often attempt to exploit these forms…
How To Manage Multiple WordPress sites
Management tools help agencies become well-oiled machines. Each task is completed with the least amount of effort and highest rate of accuracy. For people managing multiple WordPress sites, the daily…

PHP 8.3 Support Added to Staging Feature
We’ve introduced PHP version 8.3 to our staging sites. Test out new features, code changes, and updates on the latest PHP version without affecting your live website. Update PHP confidently…
How do you update and backup your website?
Creating Backup and Updating website can be time consuming and error-prone. BlogVault will save you hours everyday while providing you complete peace of mind.

Updating Everything Manually?
But it’s too time consuming, complicated and stops you from achieving your full potential. You don’t want to put your business at risk with inefficient management.

Backup Your WordPress Site
Install the plugin on your website, let it sync and you’re done. Get automated, scheduled backups for your critical site data, and make sure your website never experiences downtime again.




