How to Disable XML-RPC for Better WordPress Security
Bulletproof Backups for Your WordPress Website
Fortify your business continuity with foolproof WordPress backups. No data loss, no downtime — just secure, seamless operation.

The XML-RPC specification was developed to make it easier for different types of computers, perhaps running different operating systems or programs written in different languages, to communicate with each other over the Web. It allows developers to build programs that can interact with other programs remotely without having to learn about the underlying protocols, networking, or building complex APIs.
XML-RPC is enabled by default on WordPress since version 3.5. It can be useful for developers, but for the rest of us, it’s not worth keeping it enabled as it can introduce vulnerabilities. Besides, the WordPress REST API has replaced XML-RPC as the go-to choice for WordPress developers who want to allow other apps to interact with it remotely.
In this article, I’ll explain what XML-RPC is, why and how you should disable XML-RPC in WordPress, and the scenarios that could warrant keeping it enabled.
TL;DR: XML-RPC is a way for third-party applications to interact with your WordPress site remotely, and so it suffers from the same security issues as your login page. You can disable xml-rpc.php in WordPress to secure your site a little bit more, however, the real protection comes from having a strong WordPress security plugin like MalCare. MalCare’s firewall prevents bots, malware, and attackers from gaining access to your site, regardless of whether they try the login page or XML-RPC.
What is XML-RPC in WordPress?
XML-RPC is a specification—a set of rules essentially—that allows different types of computers to communicate over the Internet, regardless of what operating system they’re running on or what programming languages they’re compatible with. In our context, it enables WordPress and other applications to communicate with each other.
You might have heard of XML (eXtensible Markup Language) before. It’s the file format that WordPress uses to export the content of your site. RPC stands for Remote Procedure Call, a communication protocol that allows a local program to execute specific code belonging to a different program located on a different computer as if the code existed on the local program. RPC is used in several applications today, from gaming to banking. In the earlier days of WordPress, XML-RPC was what allowed one to post content from the mobile app, even though the app wasn’t running the WordPress software itself.
Anyway, the underlying code for XML-RPC is stored in a file appropriately called xmlrpc.php, in the root directory of your site. If you know how to use FTP, you’ll be able to see it. It’s still there, but it’s no longer needed since the modern REST API was integrated into WordPress. REST API is more versatile than XML-RPC, allowing WordPress to interact with many more systems than the latter allows.
How to disable XML-RPC in WordPress
After that primer on XML-RPC and learning why it makes your site a bit less secure, you might ask, “How do I disable this thing?” And that’s what I’m going to illustrate in this section. Note that disabling it isn’t a matter of simply deleting the xmlrpc.php file. That’s a WordPress core file that some 3rd-party apps and plugins still rely on to interact with WordPress, so deleting it risks disrupting their functionality. I’ll describe three ways of disabling XML-RPC safely here:
- Disable XML-RPC in WordPress using a plugin;
- Block XML-RPC using the .htaccess file; and
- Disable XML-RPC in WordPress via a filter.
Let’s take a look at each of these individually.
NOTE: Before you proceed, back up your site. We’ll be making some changes to the core WordPress files. While the methods I describe here are safe, it still helps to have a safety net should anything bad happen.
How to disable XML-RPC using a plugin
Installing a plugin is the easiest and fastest way to disable XML-RPC in WordPress. For this part of the tutorial, I’ll use the aptly named Disable XML-RPC from developer Philip Erb.
- Log in to your WordPress admin dashboard.
- Go to Plugins > Add New.
- Search for ‘Disable XML-RPC’ (developed by Philip Erb) and install it.
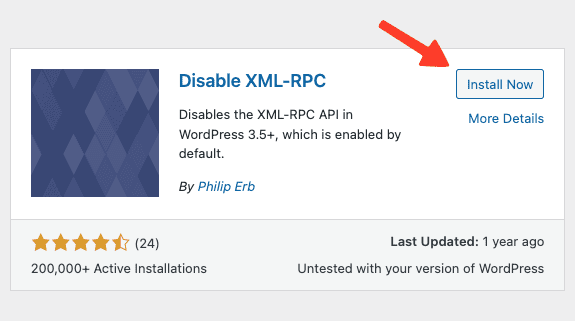
- Next, click on Activate to activate the plugin on your site and the xml-rpc.php file should be disabled
That’s it! Just like garlic can ward off vampires with its mere existence, the fact that Disable XML-RPC is active on your WordPress site is enough to keep XML-RPC disabled.
While this nuclear option will be suitable for most, if you wish to keep XML-RPC active but want to remove certain aspects of it that are abused by bad actors, then the Disable XML-RPC Pingback plugin is a better option. Unlike the plugin I mentioned above, Disable XML-RPC Pingback eliminates three functions commonly invoked by attackers (you can find the details on its official WordPress page). You’ll still have access to the rest of the file.
It works in the same way as Disable XML-RPC: simply install and activate, and you’re done.
How to block XML-RPC using .htaccess file
If you don’t like the idea of installing yet another plugin on your WordPress website, then you can disable XML-RPC in WordPress without a plugin by adding a few lines of code to the .htaccess file. If your web hosting provider uses the Nginx web server to host your site, then you won’t have access to the .htaccess file. In that case, you can contact its support team to have XML-RPC disabled for you.
To edit the .htaccess file, you can use either FTP or cPanel (or the file manager on your web hosting account if your host doesn’t have cPanel). I’ll use FTP, and FileZilla in particular, to show how to edit the file as its host-agnostic.
- Connect to your website using its FTP credentials as shown in the image below:
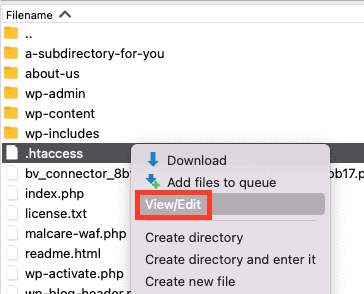
- Right-click on the .htaccess file and click on View/Edit to edit the file. Before editing the file, however, download a copy to your computer that will act as a backup.
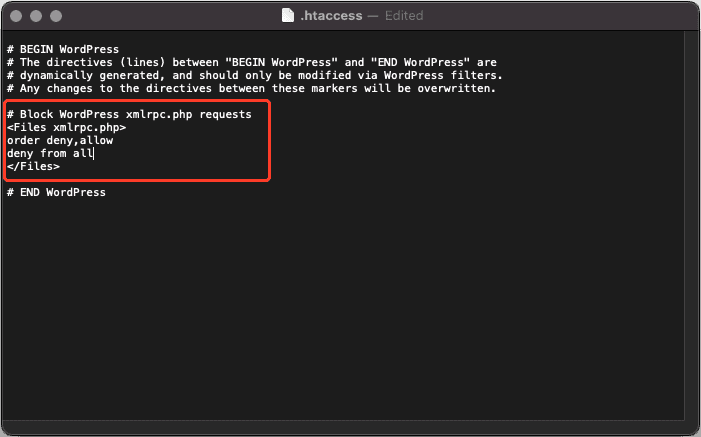
- Next, add the following lines of code to the top of the file, then save and close it:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
allow from xxx.xxx.xxx.xxx
</Files>This code snippet blocks all XML-RPC requests in WordPress apart from the IP addresses mentioned in the line that starts with “allow from.” If you wish to block requests from everyone, delete this line entirely.
How to disable XML-RPC via a custom code-based filter
Lastly, you can disable XML-RPC in WordPress manually via a filter. This method requires you to write your own plugin – called a site-specific plugin – and then add the following line of code to it:
add_filter( 'xmlrpc_enabled', '__return_false' );If you’ve never written a site-specific plugin before, check out this article to learn how to do so. Alternatively, you can add it to your theme’s functions.php file, but it’s a better practice to write a plugin instead. (When you update or change your theme, any edits you made to the functions.php file will be lost.)
Why should you disable XML-RPC.php in WordPress
While the outdated xmlrpc.php file still comes with every WordPress installation, you should disable it because it adds security vulnerabilities to your site. Now, you might wonder, if REST API has replaced XML-RPC, then why does WordPress still keep it? The main reason is backward compatibility, one of the USPs of WordPress. Automattic, the company behind WordPress, wants site owners who are either unwilling or unable to update their WordPress version to still be able to do everything they want without any hiccups.
The most common types of attacks that exploit XML-RPC are as follows:
- DDoS attacks via pingbacks. Pingback is essentially one of those comments that appear on a post when another web page links to your post. If XML-RPC is enabled, an attacker can potentially launch a DDoS attack by exploiting it to send a huge number of pingbacks to your site in a short period. The much more secure REST API makes pingbacks possible these days.
- Brute force attacks. XML-RPC sends login information over the network every time it sends a request, which makes the xmlrpc.php file a prime target for hackers.
When to keep the XML-RPC.php file enabled
There are a few scenarios where it’s wise to keep XML-RPC enabled. Here’s a list:
- You have an old website that you can’t update to version 4.4 or higher for some reason, so you don’t have access to the REST API.
- You or someone else you know uses a program that can’t access the REST API to communicate with your website.
- Integration with some 3rd party apps that can only use XML-RPC.
Conclusion
XML-RPC proved to be a useful protocol to allow apps and services to communicate with WordPress in the past. But in this day and age, the REST API has superseded it for that purpose. While WordPress still retains the xmlrpc.php file with every installation for the sake of backward compatibility, there is no reason to have it enabled anymore as it creates security vulnerabilities on your site that bad actors can exploit, barring a few uncommon scenarios. To disable XML-RPC in WordPress, you can simply install and activate the Disable XML-RPC plugin or add a few lines of code to the .htaccess file.
While disabling XML-RPC grants a slight boost to your website’s security, it’s not enough to ward off malware, DoS attacks, hacking attempts, and other ways to sabotage your site. For a comprehensive security solution for your WordPress site, look no further than MalCare. Its features include daily automatic malware scanning, one-click malware removal, a state-of-the-art integrated firewall, IP address blocking, real-time security alerts, and more. Moreover, it’s easy to find the feature you’re looking for quickly owing to its clean, minimalist UI.
FAQs
Q – What is XML-RPC in WordPress?
A – XML-RPC is a set of rules that allows different types of computers to communicate over the Internet, regardless of what operating system they’re running on or what programming languages they’re compatible with. It enables 3rd-party applications to connect remotely with WordPress.
Q – Should I disable XML-RPC?
A – Yes, you should. XML-RPC is a security hazard. It’s often exploited by attackers looking to break into your site or launch a distributed denial-of-service (DDoS) attack. Most of XML-RPC’s functionality has been superseded by the REST API anyway, so disabling it doesn’t affect your experience all that much.
Q – How can I block XML-RPC in WordPress?
A – You can disable XML-RPC by:
- Using a plugin like the Disable XML-RPC plugin;
- Adding code to block XML-RPC requests in the .htaccess file;
- Writing a site-specific plugin and adding a filter to it.
Q – Can’t I just delete the xmlrpc.php file?
A – Nope. There are some 3rd-party apps and plugins that still rely on xmlrpc.php to interact with WordPress, so deleting it could disrupt their functionality. Besides, even if you delete it, it will be recreated after a WordPress update, so it’s pointless to do so.
Tags:
Share it:
You may also like
How to Limit Form Submissions with Droip in WordPress
Forms are an indispensable part of any website because of their versatility, letting you collect information for various purposes! However, people with ill intentions often attempt to exploit these forms…
How To Manage Multiple WordPress sites
Management tools help agencies become well-oiled machines. Each task is completed with the least amount of effort and highest rate of accuracy. For people managing multiple WordPress sites, the daily…

PHP 8.3 Support Added to Staging Feature
We’ve introduced PHP version 8.3 to our staging sites. Test out new features, code changes, and updates on the latest PHP version without affecting your live website. Update PHP confidently…
How do you update and backup your website?
Creating Backup and Updating website can be time consuming and error-prone. BlogVault will save you hours everyday while providing you complete peace of mind.

Updating Everything Manually?
But it’s too time consuming, complicated and stops you from achieving your full potential. You don’t want to put your business at risk with inefficient management.

Backup Your WordPress Site
Install the plugin on your website, let it sync and you’re done. Get automated, scheduled backups for your critical site data, and make sure your website never experiences downtime again.




