htaccess and security plugins
Bulletproof Backups for Your WordPress Website
Fortify your business continuity with foolproof WordPress backups. No data loss, no downtime — just secure, seamless operation.
.htaccess is a configuration file for use on web servers like Apache. It helps site owners and administrators control how visitors interact with the site. A web server generally comes with preset configurations that determine various parameters on your site. They include access control, URL rewrites, conditional blocking, etc. Quite often, you may want to alter these parameters by disabling directory browsing or blocking certain IPs. However, in most cases, you wont have access to the main server configuration file, especially in the case of shared hosting. By adding directives to the htaccess file, you can effectively override the underlying configuration on your web server. This file is also useful when you want to enable/disable certain functionality specific to a directory or sub-directories within it.
The htaccess file also plays a vital role when it comes to your site’s security. You can protect important files or hide pages by adding simple rules to this file. Hence it is no surprise that security plugins also modify htaccess files extensively to enhance your site’s security. While some plugins add a set of htaccess rules at one go, others are specific to certain features/ settings.
Modifying htaccess is no easy task. One tiny error can result in breaking a lot of things on your site. Same is the case when security plugins modify your site’s htaccess file. We’ve seen many cases where plugins that extensively modify the htaccess files have resulted in breakages. Hence it is recommended that you always backup htaccess files prior to making any changes.
Once you have installed a plugin on your site and find that something’s wrong, it is a huge challenge to narrow down on the root cause. For instance, the BulletProof Security plugin adds 100s of lines to the htaccess file in your root directory. Unless you are familiar with the terminology, it is extremely hard for a layman to figure out what these rules mean. In this article, we uncover the association between htaccess and security plugins. So the next time you suspect an issue with one of the htaccess rules, you’ll be better equipped to analyze them and arrive at a solution quickly.
Protecting Important Files
Denying access to important WordPress files is something every security plugin does. The common ones are htaccess and wp-config.php. By adding the following rules, anyone trying to access this file through any means (like a browser) will be unable to do so. The BulletProof Security plugin adds the following set of rules to achieve this –
<FilesMatch “^(wp-config\.php|php\.ini|php5\.ini|readme\.html|bb-config\.php)”>
Order Allow,Deny
Deny from all
#Allow from x.x.x.x
</FilesMatch>
As per the above directive, access to a filename that matches any of on the list is denied. You can specify the admin IP address as an exception to the rule.
The iThemes Security plugin, on the other hand, adds individual rules for every file as follows –
<files .htaccess>
Order allow,deny
Deny from all
</files>
<files readme.html>
Order allow,deny
Deny from all
</files>
<files readme.txt>
Order allow,deny
Deny from all
</files>
<files install.php>
Order allow,deny
Deny from all
</files>
<files wp-config.php>
Order allow,deny
Deny from all
</files>
Irrespective of which method is followed, this is a handy tip that’ll secure important files on your server.
Disabling Directory Browsing
Most web servers (like Apache) allow directory browsing by default. This is a server setting which lets visitors list the contents of a directory in the absence of an index page. This is completely unsafe for any site owner as it would expose the location of important files on the site. Attackers may then view the contents of restricted files, like wp-config.php and gain access to your site. Nearly every security plugin like BulletProof Security, iThemes Security, etc enable disable directory browsing by adding the following line to your htaccess file –
Options –Indexes
This is a very useful trick that’ll hide your directory listing from prying eyes.
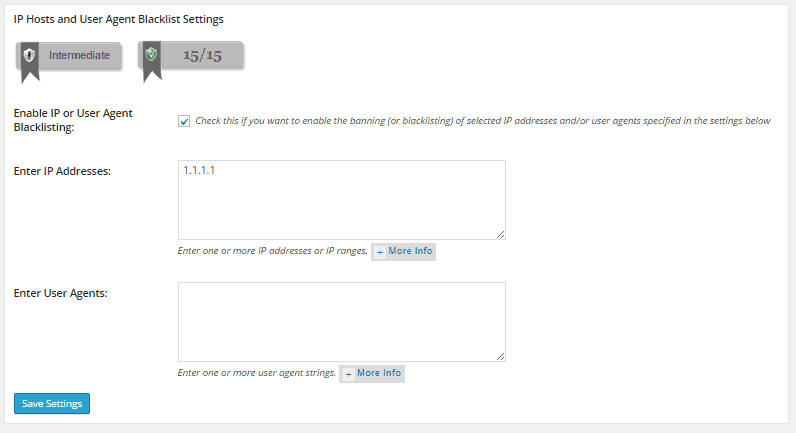
Blacklisting IPs
Some security plugins allow users to add IPs to a blacklist that’ll be blocked from accessing your site. The All In One WP Security is one such plugin that lets you blacklist IPs using htaccess.
Order allow,deny
Allow from all
Deny from 1.1.1.1
The drawback with this technique is that it can be too hard to manage over time. Moreover when automated bots are used to launch attacks, it is all too easy for them to keep changing the IP address and circumvent such checks.
Disabling PHP execution
Certain folders in WordPress are writeable (e.g. uploads) and allow users to upload images, videos and other files to your site. Such folders are often exploited by attackers to upload their own malicious code and execute it remotely. Security plugins mitigate this problem by doing away with execute permissions on such folders. That way, even if an attacker manages to upload malicious code onto your site, he will be unable to execute it. There are multiple ways to achieve this. The iThemes Security plugin adds a Rewrite rule specific to uploads folder –
RewriteRule ^(.*)/uploads/(.*).php(.?) – [F]
Another way is to create an htaccess file in the specific directory, e.g. uploads, and add the following rule to it –
<FilesMatch “\.(php|php\.)$”>
Order Allow,Deny
Deny from all
</FilesMatch>
The All In One WP Security plugin disables XML RPC by adopting a similar approach –
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
This is a very useful security feature that must be adopted by every site. It is very effective in preventing remote code execution attacks like TimThumb and Mailpoet.
Blocking Unwanted HTTP REQUEST methods
The HTTP protocol that is used to exchange information between your browser and server supports various request methods. The typical GET and POST methods are used to retrieve information from and send information to the server respectively. Apart from these methods, there are many others like HEAD, TRACE, DEBUG, and DELETE that are also supported by HTTP. However, these are only meant for certain exceptions. Most of the current browsers, however, don’t support methods other than POST and GET in HTML forms. Neither does WordPress. Hence we can block such requests, which are most likely created using scripts, by adding the following lines to htaccess. This is followed by nearly all the popular security plugins –
RewriteCond %{REQUEST_METHOD} ^(TRACE|DELETE|HEAD|DEBUG) [NC]
RewriteRule ^(.*)$ – [F]
A useful trick that is must have in your htaccess.
Disabling Server Signature
Just like WordPress, every web server has a version associated with it. Whenever an error page is generated on your site (e.g. 404 page not found), the server signature (version and port details) is also displayed. Once the server version is revealed, attacks can exploit vulnerabilities that exist in a specific version. To avoid this, most popular security plugins such as BulletProof Security, iThemes Security, and All In One WP Security add a rule in htaccess that disables server signature.
ServerSignature Off
Though the rule works as expected, it is hardly needed these days. Every theme in WordPress comes with custom error pages. These pages are used to display user-friendly error messages and don’t include any server details.
Blocking Suspicious URLs
A URL is primarily used to denote a web address while browsing the Internet. However, the URL can include many other details such as path to a resource on your site (e.g. page.html), port number, and a query string. The query string is used to pass additional information to the server by the browser. For example,
http://mysite.com/over/here?name=myquery
When a visitor types such a URL on his browser, a lot of additional information is included in this request. One of them is the HTTP_USER_AGENT, which can be used to block bad bots from your site. All the popular security plugins block the known list of bad bots by adding the following directive –
RewriteCond %{HTTP_USER_AGENT} (havij|libwww-perl|wget|python|nikto|curl|scan|java|winhttp|clshttp|loader) [NC,OR]
RewriteCond %{HTTP_USER_AGENT} (%0A|%0D|%27|%3C|%3E|%00) [NC,OR]
RewriteCond %{HTTP_USER_AGENT} (;|<|>|’|”|\)|\(|%0A|%0D|%22|%27|%28|%3C|%3E|%00).*(libwww-perl|wget|python|nikto|curl|scan|java|winhttp|HTTrack|clshttp|archiver|loader|email|harvest|extract|grab|miner) [NC,OR]
RewriteRule ^(.*)$ – [F]
THE_REQUEST variable represents the full HTTP request line sent by the browser to the server (e.g., “GET /index.html HTTP/1.1”). This is often exploited by attackers to access files/ folders that contain sensitive information such as /etc/passwd and cgi-bin. Security plugins protect against malicious requests and other exploitative behavior by checking the variable for prohibited characters and important directory paths.
RewriteCond %{THE_REQUEST} (\?|\*|%2a)+(%20+|\\s+|%20+\\s+|\\s+%20+|\\s+%20+\\s+)HTTP(:/|/) [NC,OR]
RewriteCond %{THE_REQUEST} etc/passwd [NC,OR]
RewriteCond %{THE_REQUEST} cgi-bin [NC,OR]
RewriteCond %{THE_REQUEST} (%0A|%0D|\\r|\\n) [NC,OR]
RewriteRule ^(.*)$ – [F]
Blacklisting via the HTTP_REFERER variable is another excellent way to defend against attacks and protect against malicious activity. The HTTP_REFERER tells you the source of an incoming link to a web page. By looking for known offenders, you can effective block them out of your site. Security plugins such as BulletProof Security add the following rules to achieve this –
RewriteCond %{HTTP_REFERER} (%0A|%0D|%27|%3C|%3E|%00) [NC,OR]
RewriteCond %{HTTP_REFERER} \.opendirviewer\. [NC,OR]
RewriteCond %{HTTP_REFERER} users\.skynet\.be.* [NC,OR]
RewriteRule ^(.*)$ – [F]
The query string has been exploited by attackers to launch SQL injection attacks. Attackers insert malicious code as part of the URL’s query string which gets executed by the server to wreck havoc on our sites. We can prevent such attacks by blocking suspicious URLs on our site. Security plugins use a bunch of conditions to protect our sites such attacks. These rules are effective in blocking SQL injection attacks, local file inclusion attacks, and base64 attacks. Security plugins use the QUERY_STRING variable to check all query string input against a list of prohibited alphanumeric characters strings. This strategy will deny access to any URL-request that includes a query-string containing localhost references, invalid punctuation, hexadecimal equivalents, and various SQL commands.
RewriteCond %{QUERY_STRING} [a-zA-Z0-9_]=http:// [NC,OR]
RewriteCond %{QUERY_STRING} [a-zA-Z0-9_]=(\.\.//?)+ [NC,OR]
RewriteCond %{QUERY_STRING} [a-zA-Z0-9_]=/([a-z0-9_.]//?)+ [NC,OR]
RewriteCond %{QUERY_STRING} \=PHP[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12} [NC,OR]
RewriteCond %{QUERY_STRING} (\.\./|%2e%2e%2f|%2e%2e/|\.\.%2f|%2e\.%2f|%2e\./|\.%2e%2f|\.%2e/) [NC,OR]
RewriteCond %{QUERY_STRING} ftp\: [NC,OR]
RewriteCond %{QUERY_STRING} http\: [NC,OR]
RewriteCond %{QUERY_STRING} https\: [NC,OR]
RewriteCond %{QUERY_STRING} \=\|w\| [NC,OR]
RewriteCond %{QUERY_STRING} ^(.*)/self/(.*)$ [NC,OR]
RewriteCond %{QUERY_STRING} ^(.*)cPath=http://(.*)$ [NC,OR]
RewriteCond %{QUERY_STRING} (\<|%3C).*script.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} (<|%3C)([^s]*s)+cript.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} (\<|%3C).*embed.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} (<|%3C)([^e]*e)+mbed.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} (\<|%3C).*object.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} (<|%3C)([^o]*o)+bject.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} (\<|%3C).*iframe.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} (<|%3C)([^i]*i)+frame.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} base64_encode.*\(.*\) [NC,OR]
RewriteCond %{QUERY_STRING} base64_(en|de)code[^(]*\([^)]*\) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} ^.*(\(|\)|<|>|%3c|%3e).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(\x00|\x04|\x08|\x0d|\x1b|\x20|\x3c|\x3e|\x7f).* [NC,OR]
RewriteCond %{QUERY_STRING} (NULL|OUTFILE|LOAD_FILE) [OR]
RewriteCond %{QUERY_STRING} (\.{1,}/)+(motd|etc|bin) [NC,OR]
RewriteCond %{QUERY_STRING} (localhost|loopback|127\.0\.0\.1) [NC,OR]
RewriteCond %{QUERY_STRING} (<|>|’|%0A|%0D|%27|%3C|%3E|%00) [NC,OR]
RewriteCond %{QUERY_STRING} concat[^\(]*\( [NC,OR]
RewriteCond %{QUERY_STRING} union([^s]*s)+elect [NC,OR]
RewriteCond %{QUERY_STRING} union([^a]*a)+ll([^s]*s)+elect [NC,OR]
RewriteRule ^(.*)$ – [F]
The above rules are supported by all the popular security plugins as they are extremely effective in mitigating a number of common attacks.
Protecting wp-includes
The wp-includes folder includes many important scripts that aren’t meant to be accessed by users. Hence it is highly recommended that these scripts are blocked from execution using a set of htaccess rules. Nearly all security plugins include this layer of protection by adding the following lines –
RewriteRule ^wp-admin/includes/ – [F]
RewriteRule !^wp-includes/ – [S=3]
RewriteCond %{SCRIPT_FILENAME} !^(.*)wp-includes/ms-files.php
RewriteRule ^wp-includes/[^/]+\.php$ – [F]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php – [F]
RewriteRule ^wp-includes/theme-compat/ – [F]
If done right, htaccess can be used very effectively to boost your site’s security. It helps you add many additional layers of protection by using simple tricks. However, you must exercise extreme caution while modifying this file as something as tiny as an extra space can end up breaking parts of your site. It’s best to take a complete website backup before making any modifications in the htaccess file.
Hope this article will bail you out of those sticky situations when something has gone wrong.
Tags:
Share it:
You may also like
How to Limit Form Submissions with Droip in WordPress
Forms are an indispensable part of any website because of their versatility, letting you collect information for various purposes! However, people with ill intentions often attempt to exploit these forms…
How To Manage Multiple WordPress sites
Management tools help agencies become well-oiled machines. Each task is completed with the least amount of effort and highest rate of accuracy. For people managing multiple WordPress sites, the daily…

PHP 8.3 Support Added to Staging Feature
We’ve introduced PHP version 8.3 to our staging sites. Test out new features, code changes, and updates on the latest PHP version without affecting your live website. Update PHP confidently…
How do you update and backup your website?
Creating Backup and Updating website can be time consuming and error-prone. BlogVault will save you hours everyday while providing you complete peace of mind.

Updating Everything Manually?
But it’s too time consuming, complicated and stops you from achieving your full potential. You don’t want to put your business at risk with inefficient management.

Backup Your WordPress Site
Install the plugin on your website, let it sync and you’re done. Get automated, scheduled backups for your critical site data, and make sure your website never experiences downtime again.