14 Best WordPress Security Practices to Protect Your Site
Bulletproof Backups for Your WordPress Website
Fortify your business continuity with foolproof WordPress backups. No data loss, no downtime — just secure, seamless operation.

WordPress security is important for any high-value website.
Hackers often target WordPress sites for a number of reasons such as using the website resources, accessing the data, using the website to target visitors with phishing scams, and more. But is there anything you can do about it?
Yes. You can take measures that help you secure a WordPress site from these malicious actors and protect your visitors and data.
TL;DR: Follow our guide to secure your WordPress site and for a hassle-free solution, install MalCare. MalCare helps you protect a WordPress site from hackers preemptively as well as after an attack. You can schedule scans, conduct cleanups, and ward off malicious traffic easily with MalCare
What is WordPress Security?
WordPress security can be explained as a series of measures taken to protect a WordPress site from hackers, external threats, and attacks.
Given that WordPress is a popular CMS, it enjoys a lot of attention—good and bad. Hackers are always on the lookout to find vulnerabilities in websites to exploit them, and even the smallest lapse in security can give them an opening.
The good news, however, is that there are ways to protect your site. And you can maintain the security of your site simply by taking a few effective WordPress security measures.
14 Best WordPress Security Practices to Protect Your Site From Hackers
If you look up WordPress security, you will be bombarded with advice. What you need to keep in mind is that not all of it is good advice. Some common advice, like changing the default admin username, makes very little difference, whereas some are outright harmful.
So how do you know what measures are actually useful to secure your site? You need to be able to distinguish expert sources from those that are simply putting content out without testing.
We have listed the 14 WordPress security best practices that we have found to be most effective. These measures are proven to make a difference in terms of website security.
1. Install a WordPress security plugin
Using a security plugin is a far better alternative to manual security measures. It helps you automate security, comes with security expertise, and guarantees peace of mind. A WordPress security plugin like MalCare is the amalgamation of the expertise of several experts who have worked on WordPress security for years. The plugin automates security for your WordPress site so that you don’t have to worry about the small things.
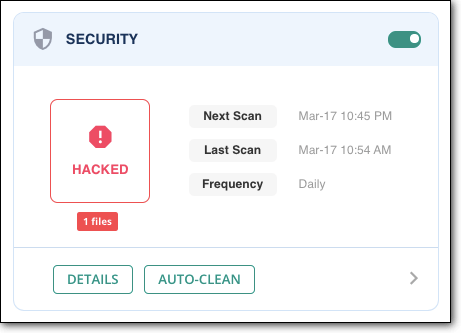
Most importantly, you can schedule automated scans on your WordPress website with MalCare. This will help you stay on top of your WordPress security. MalCare also offers several other security features like one-click malware cleanup, firewall protection, vulnerability detection, and more. There is no better way to secure your WordPress website than to install MalCare on your WordPress site.
2. Invest in a web application firewall
No matter the number of visitors on your site, a part of your traffic is always malicious. This could be bad bots trying to break into your site with brute force attacks, or hackers trying to find backdoors and vulnerabilities. It’s impossible to stop all of the malicious traffic entirely, but you can ward off most of it with a firewall.
A web application firewall, such as that of MalCare will help you limit login attempts, block malicious IPs, help you block IPs from entire regions, and ensure that your website is protected from malicious actors.
3. Deep scan your website daily
We have already discussed that installing a WordPress security plugin will help you scan your website regularly. But even if you choose not to go with a security plugin, scanning your website daily is still absolutely pertinent.
Hacks and malware get worse the longer they stay on your website. If your website is hacked, and you find the hack right away, the hackers won’t have time to cause much damage. However, if malware is on your website for a long duration, it can redirect your visitors, steal your data, attack your customers, deface your website, or even completely hijack your site.
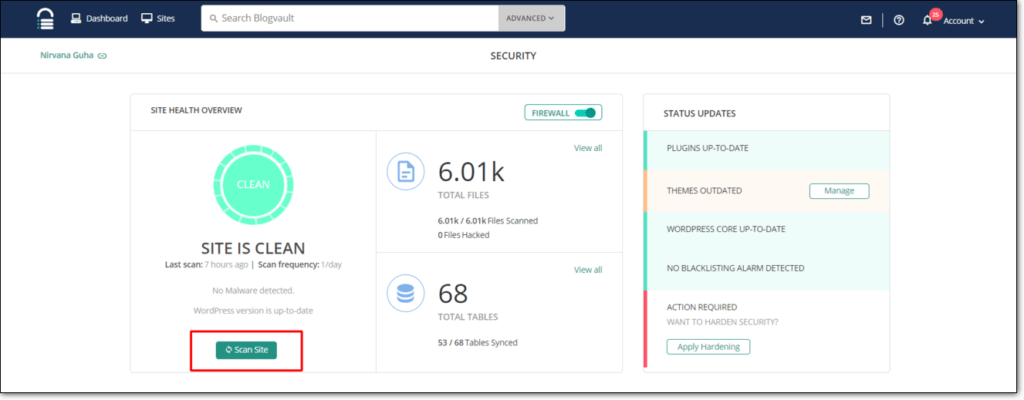
This is why hackers make sure that malware remains hidden from the website admin for as long as possible. The only way to confirm the presence of malware is by scanning your website every day. MalCare’s advanced scanner is one of the only scanners available that can detect even the best hidden malware on your WordPress site. It also allows you to schedule scans and sends you real-time alerts if any suspicious activity is detected. What more, MalCare’s intelligent algorithm ensures that there are no false positives or false negatives. This means that you will not receive alerts for non-malware and neither will malware go undetected.
4. Backup your website every day
Backups are extremely important for your website overall. Not just from a security perspective, but also from a functionality perspective. If tomorrow your website gets hacked and you lose all the data, you will have to start from scratch again. Unless you have backups. Backups allow you to restore your site to a particular point of time so that no matter what goes wrong, whether it’s malware or broken updates, you can always get your site up and running again.
Using a backup solution like BlogVault allows you to schedule backups daily or in real-time so that you never lose a big chunk of data. BlogVault also stores your backups on an offsite server so that if your website server is compromised, your backups are still safe.
5. Make sure your WordPress site is updated
Updates are a large part of your WordPress security. Most people think that updates only add new features to WordPress or extensions. While adding features or removing bugs is an important objective of updates, the primary objective is to ensure WordPress security.
WordPress releases a major update every 152 days, and plugins and themes are frequently updated. These updates often carry patches to discovered vulnerabilities, which otherwise can be exploited by hackers. Therefore, it is important that you keep your WordPress site updated as frequently as possible.
Many website admin delay updates because updates can prove to be pesky and interact erratically with other elements on the site. In some cases, they can even break the site. For major updates, you can use a staging site to test updates first, and then merge them with your live site after thorough testing.
Here is our complete guide on how to update the WordPress site.
6. Ensure strong password requirements
Weak passwords are one of the most common reasons for websites getting hacked. And given that it is an easily fixable problem, it should be a priority. In order to make sure that your passwords are not the reason for your WordPress site getting hacked, you need to enforce strong password policies.
- Use a strong password that uses small case and capital case letters, numbers, symbols, and punctuation.
- Use a password manager to use and remember strong passwords.
- Use a password policy plugin to enforce strong passwords for all users.
- Frequently update all your passwords.
- Do not reuse passwords for multiple accounts.
- Do not share your passwords with anyone in any case.
7. Use two-factor authentication
Two-factor authentication is a security method that adds an added layer of protection to the login process on your website. Two-factor authentication, or 2FA, asks for two keys from the user in order to grant them access. One is a password and the other key is usually generated in real-time, such as an OTP.
This ensures that in case a hacker gets access to your credentials, they still cannot access your website with just the password. This is also a useful method to stop brute force attacks.
8. Install SSL on your WordPress site
SSL is a security protocol for websites that encrypts all the interaction to and from your website server. If you have SSL installed on your site, even if someone intercepts this interaction, they won’t be able to use the information. This protects your website data, credentials, and other sensitive information from falling into the wrong hands.
Here’s how to install SSL certificate in WordPress.
9. Pick the right web host
Your web host is the one who maintains your website server. Therefore, choosing a good web host is extremely important. While the chances of your website getting hacked due to your web host is rare, it’s not unheard of. If your web host does not take adequate measures to secure their servers, there is always a chance that your site will be vulnerable.
Additionally, web hosts can be trigger-happy when it comes to deleting websites if they detect malware. A good web host should be able to quarantine infected websites without causing deleting the data entirely. So it is necessary to choose a good fit.
10. Harden WordPress
WordPress suggests a string of measures to secure your WordPress website. This includes using two-factor authentication, limiting login attempts, and more. These measures are collectively known as WordPress hardening, and it is a good idea to implement these measures to strengthen your site’s security.
If you use MalCare, you can implement WordPress hardening with the click of a button, or you can also do it manually.
11. Remove unused themes and plugins
Website admin often install several themes and plugins that they need for a particular task.. These extensions are rarely removed from the site after their purpose is served. The problem with this is that admin don’t really bother updating the extensions that they use. So if a vulnerability is discovered, it remains on your site as it is.
Hackers can exploit these vulnerabilities to gain access to your site. Therefore, it is best to remove any unused themes and plugins entirely.
NOTE: If you have any nulled software on your site, get rid of it immediately. Nulled themes and plugins are riddled with malware and backdoors, and are an invitation for hackers to attack your site.
12. Implement user management policies
It is not enough to secure just your admin account. Hackers can gain access to your site through user accounts as well, which is why implementing strong user management policies is necessary.
- Enforce strong user passwords.
- Use a password policy plugin to enforce frequent updates
- Use the least privileges policy for users.
- Check the activity log to ensure no user privileges have been escalated.
Implementing these policies will help you retain control over your website and help you reduce any security incidents.
13. Use SFTP/SSH for transfer of files
If you use FTP for any kind of changes to your WordPress site, opt for SFTP instead. SFTP functions exactly in the same way as FTP but when you transfer any files, they are transferred over SSH, which is a secure protocol.
If you don’t use FTP and this sounds like a ton of technical jargon, don’t worry. This is a measure only for those who use FTP for any kind of transfer.
14. Manage multiple WordPress installations
Sometimes you may have multiple WordPress installations on your website. It could be in the form of a sub-domain or a staging site, but multiple WordPress installations on a site can cause several WordPress security issues.
This poses the same issue as having unused or inactive themes on your site. Older WordPress installations can be vulnerable, and given that people tend to overlook updating inactive installations, these vulnerabilities will stay on your site.
In case of a hack, even if you clean up your primary site, the nested WordPress installations can still cause the malware to reoccur because these vulnerabilities can still be exploited by hackers and the malware can spread across files. We suggest that you either remove unused installations or maintain these as you would your primary site.
Why WordPress Security is Important
WordPress security is not just necessary to avoid hacks, it is important to avoid the far-ranging consequences of malware. A lapse in security can cause several issues for WordPress admin such as:
- Site getting blacklisted by Google
- Web host suspending site
- Drop in organic traffic
- Loss in revenue
- Legal issues
- Customers losing trust in business
- Data loss and theft
This list is not exhaustive by any means and malware can be nightmarish if not handled in time. It is best to take the right precautions and to avoid dealing with it entirely.
Final Thoughts
The security of your WordPress site should be your number one priority because the alternative is to deal with the losses and piled-up expenses caused by malware.
These WordPress security tips will help you secure your site without having to scratch your head about where to start. The best and easiest way to secure your WordPress site is to install MalCare and let it take charge of your website security.
FAQs
How do I improve my WordPress website security?
The easiest way to improve your WordPress security is to install a security plugin like MalCare that has a malware scanner, firewall, and clean-up features. MalCare offers complete security to WordPress sites without affecting performance.
What is the best WordPress security?
The best WordPress security solution is the one that fits your website’s requirements. Broadly speaking, a security solution needs to have an effective scanner, a firewall, and cleanup features. MalCare offers all of these features and more so that your website is secure from malicious actors.
Is WordPress safe from hackers?
WordPress is a secure platform by itself. However, given the popularity of the platform, it attracts attention. Hackers tend to focus their efforts on WordPress sites because there are so many of them. Even though WordPress sites are often targeted, most sites are vulnerable because they aren’t protected at all. With a few simple measures like using strong passwords and installing a security plugin, you can secure your WordPress site from hackers.
Tags:
Share it:
You may also like
How to Limit Form Submissions with Droip in WordPress
Forms are an indispensable part of any website because of their versatility, letting you collect information for various purposes! However, people with ill intentions often attempt to exploit these forms…
How To Manage Multiple WordPress sites
Management tools help agencies become well-oiled machines. Each task is completed with the least amount of effort and highest rate of accuracy. For people managing multiple WordPress sites, the daily…

PHP 8.3 Support Added to Staging Feature
We’ve introduced PHP version 8.3 to our staging sites. Test out new features, code changes, and updates on the latest PHP version without affecting your live website. Update PHP confidently…
How do you update and backup your website?
Creating Backup and Updating website can be time consuming and error-prone. BlogVault will save you hours everyday while providing you complete peace of mind.

Updating Everything Manually?
But it’s too time consuming, complicated and stops you from achieving your full potential. You don’t want to put your business at risk with inefficient management.

Backup Your WordPress Site
Install the plugin on your website, let it sync and you’re done. Get automated, scheduled backups for your critical site data, and make sure your website never experiences downtime again.




