The Price of Popularity: Why Hackers Target WordPress
Bulletproof Backups for Your WordPress Website
Fortify your business continuity with foolproof WordPress backups. No data loss, no downtime — just secure, seamless operation.
WordPress is the fastest-growing, most popular CMS in the world because of its user-friendly features, but this also puts a target on its back. Why is WordPress popular with hackers?
Whether it’s a simple blogger writing about college experiences, or the Time Magazine, WordPress is the choice CMS for anyone looking to publish content on a website. And for good reason too: WordPress is not only Open Source, it’s extensible, flexible and it’s also supported by a community that actively contributes.
How popular is WordPress?
WordPress is currently the most used, and the fastest-growing CMS in the world. And according to data from W3Tech for August 2016, 246 WordPress sites were added to the internet every day.
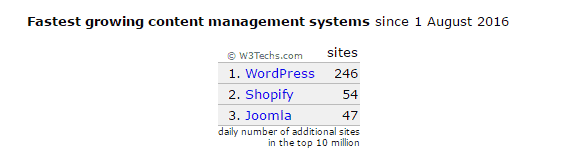
By September 2016, this number had only increased:
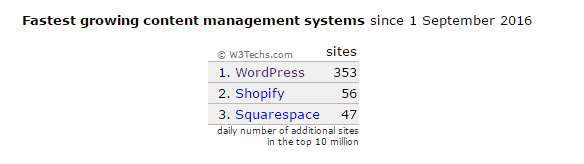
This illustrates the rapid pace at which WordPress is growing, and that the rates of its use have continued to grow. Considering all the features that make WordPress popular, it’s not surprising how the CMS got to this position, and why it will grow more rapidly.
After all, the CMS is Open Source meaning that it is transparent to anyone who wants to learn how to use it effectively, while also offering a number of alternatives that help make it convenient, extensible and functional. What makes it the most popular amongst other Open Source CMSes like Joomla and Drupal, though, is the fact that it is more user-friendly. WordPress requires lesser technical knowledge than any other Open Source CMS, and is a lot simpler to use in that regard.
WordPress’ popularity makes it an obvious target
WordPress started out as a publishing platform that only needed basic technical knowledge to handle. This is what made WordPress popular. However, it didn’t stop at that. The more users it acquired, the more was created for it by the community. The add-ons created made WordPress more flexible, and more functional. This meant it became more widely used.
Data from W3Techs shows that of all the websites in the world, 54.6% don’t use a CMS at all.
Of the rest that do rely on a CMS (45.4%), WordPress powers 26.7%, meaning it is the base for 58.9% of all websites that run on a CMS.
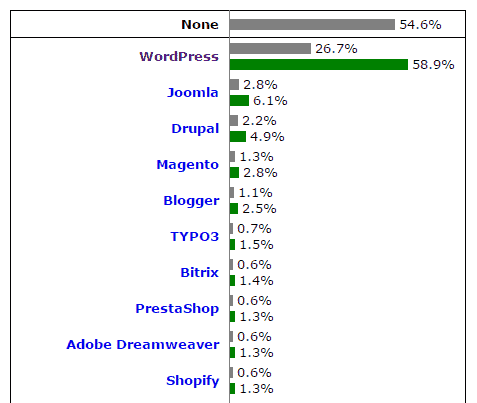
Having more users than any other CMS put a target on WordPress’ back… similar to how the Windows Operating System was targeted when it was still new.
Back then, since the OS was so widely used, hackers targeted vulnerabilities that the developers hadn’t foreseen. This ensured that more users could potentially be affected by a single hack. All the hackers needed to do, was to ensure that the malicious files were made accessible to the users. With WordPress this isn’t a concern since all a hacker has to do, is to find a way to automate an exploit.
Most hacks are automated, which means they don’t need the hacker’s intervention. The hacker only programs a crawler bot to run malicious code when it finds vulnerabilities that allow it to run. The bot then replicates the exploit on other sites that have the same common vulnerability. This could lead to millions of sites getting compromised at a time.
Reason #1: Wide scope, more damage
According to WordPress, there are about 22.9 million page views on WordPress sites per month. This makes WordPress an attractive target for hackers’ attacks. The way they see it, the more the audience, the more the potential damage an attack can incur.
Hackers perform exploits for a number of reasons, so the scope of this damage can vary, but what they aim for, is to gain the most out of a single exploit; whether it is visibility, information or resources.All it takes to hit the jackpot, is one unique, undetectable exploit.
One example of this, was the case of TimThumb (an image-to-thumbnail resizing plugin) which was so popular that a number of themes had it bundled with their offering. So users didn’t even have to install the plugin for their site to be vulnerable. If they were unaware that theme being used on their WordPress site was using the plugin then they would be sitting ducks. When it was exploited, a number of users got hacked because they didn’t even know that they had the malicious code on their sites.
Moreover, with attacks like Cross-site Scripting (XSS), all it takes for malicious code to propagate, is people simply visiting the infected sites, or using them. Attacks like these maximise the range of the damage, and spread exponentially.
Reason #2: WordPress has all sorts of users
WordPress sites can host anything from a forum to an e-commerce site, with the help of add-ons (plugins, themes and widgets). This makes the CMS extremely popular amongst users.
Even those who are code-illiterate can perform basic modifications to their site, and publish content. However, what most users don’t expect, is the amount of work, and technical expertise it takes to maintain a WordPress site. Maintaining a fairly secure WordPress site requires great attention to detail, and perseverance, especially since simply updating an add-on on the site could lead to the whole site crashing. Not performing the update, on the other hand, would leave the site vulnerable to attacks. Users, therefore have to acquaint themselves with the basics of a WordPress site, such as the parts of a site, what they contain, and how to test updates before updating them… Or at least invest in a WordPress backup solution that is reliable, and sensible. However, since a considerable portion of the WordPress community of users doesn’t have the technical know-how or time required, they are easy targets. What makes this scenario worse, is the fact that a large portion of the community are novices who are ignorant of how hacks work, or what could make a website insecure.
Another factor to consider, is that WordPress users with the right amount of technical know-how they can modify their installations of WordPress to suit their needs. Those who don’t have the expertise or time, however, rely heavily on plugins for added functionality. This leads to vulnerabilities, since not every plugin or theme is coded according to WordPress standards. This allows hackers a lot of room– any one outdated plugin could be exploited easily. And again, if the plugin is widely used, then all they have to do to exploit multiple sites is identify the sites that use the vulnerable version and replicate the exploit.
Reason #3: WordPress has all sorts of developers
Since it runs on the Open Source philosophy, WordPress has everyone from the community contributing code to it, from novices to experts.
This means users who have only just started experimenting with code, contribute alongside hobbyists, expert developers, and third-parties too (who code premium add-ons made available on websites like ThemeForest). Every contributor can access resources from the community, such as the WordPress Codex, forums, and other websites, but there is no way to make sure that the contributors follow them. This obviously means there is room for error, which makes WordPress a low-hanging fruit for hackers.
Added to this, WordPress runs on a ‘security through transparency’ model, which means that everything: every vulnerability, where it was found and security patches are all announced to the community. Hackers, therefore, don’t even need to put in the effort to find vulnerabilities or how they work. All they have to do, is scan the WordPress community for news, and put two and two together to exploit websites that are still vulnerable. The situation is exacerbated by the fact that WordPress users, due to maintenance issues, don’t usually update to patches as fast as they should.
So is WordPress safe?
Going back to our Windows analogy, in spite of the system quickly adapting, people still perceive it as being insecure when compared to Linux-based Operating Systems. This is because hackers target it since it has the most users. The same applies to WordPress.
All of the reasons mentioned above do not mean that WordPress is in itself vulnerable to attacks; in fact, there haven’t been any major exploits on WordPress core because of how stringent quality control is with the core.
However, more vulnerabilities are reported on WordPress, because of how ‘security through transparency’ on WordPress works. This gives an illusion that the CMS isn’t safe, but to be fair, there is no such thing as a secure website. WordPress is susceptible to hacks because of a number of factors, such as the varied demographic of its user and developer base, but following simple security measures eliminate a number of risks, and entry points.
Since hacks are such a prevalent threat, the wisest security measure, would be to invest in an intelligent malware scanner and hack cleaner designed especially for WordPress, like MalCare.
Tags:
Share it:
You may also like
How to Limit Form Submissions with Droip in WordPress
Forms are an indispensable part of any website because of their versatility, letting you collect information for various purposes! However, people with ill intentions often attempt to exploit these forms…
How To Manage Multiple WordPress sites
Management tools help agencies become well-oiled machines. Each task is completed with the least amount of effort and highest rate of accuracy. For people managing multiple WordPress sites, the daily…

PHP 8.3 Support Added to Staging Feature
We’ve introduced PHP version 8.3 to our staging sites. Test out new features, code changes, and updates on the latest PHP version without affecting your live website. Update PHP confidently…
How do you update and backup your website?
Creating Backup and Updating website can be time consuming and error-prone. BlogVault will save you hours everyday while providing you complete peace of mind.

Updating Everything Manually?
But it’s too time consuming, complicated and stops you from achieving your full potential. You don’t want to put your business at risk with inefficient management.

Backup Your WordPress Site
Install the plugin on your website, let it sync and you’re done. Get automated, scheduled backups for your critical site data, and make sure your website never experiences downtime again.




