All you ever wanted to know about Brute Force Attacks
Bulletproof Backups for Your WordPress Website
Fortify your business continuity with foolproof WordPress backups. No data loss, no downtime — just secure, seamless operation.
Brute force attacks on WordPress have increased manifold in the past few years. Also known as password-guessing or dictionary attack, they use a systematic trial and method approach where every combination is used to crack your password. If you have a site that includes login authentication, you’re a likely target for attack. That covers almost all the WordPress sites, amounting to a large percentage of the Internet.
The primary objective of a brute force attack is access to your admin account. Once the attackers have breached your login, they gain unrestricted access to your site’s resources. They can use your site for economic gains, denting your brand, or simply gaining popularity. In this form of attack, the evil-doers use bots that are configured to look for preset defaults, for example, the admin username. Once a match is found, the bot will initiate an attack by making indefinite attempts to crack the admin password. The attackers are usually unaware of whom they are attacking until the attack is successful. Talk of complete automation, huh?
Best Practices to prevent Brute Force Attacks
The following are the top 3 steps that every WordPress site owner must take to protect against brute force attacks. They are quite simple to follow, yet very effective in their purpose.
Using Strong Passwords
Using strong passwords is one of the best practices recommended by any security expert. As per a recent statistics report, people most commonly use passwords like abc123, qwerty, 123456 that are oh-so-easy to crack. Unbelievable, yet true. The bots used by the attackers can crack such weak passwords within a few tries. In the case of a strong password, a bot will take a million attempts to get anywhere close. So always remember to use long unpredictable passwords, avoid dictionary words, avoid reusing passwords, and change passwords regularly.
Renaming the Admin User
Hackers first look for the default username admin. Once found, they will try to crack your password to gain full control of your site. You can make their job harder by renaming the admin username to something that’s unique. Now the hackers have an additional task to first guess your username before attempting to crack your password.
It doesn’t end here though. Merely changing the username might not suffice. The admin account is associated with user ID 1 by default. In our article on How to change the user ID of your admin account , we saw how this user ID can be used to identify the corresponding username. Hence it is always better to change the user ID along with the username for the admin account.
Rate Limiting the Login Attempts
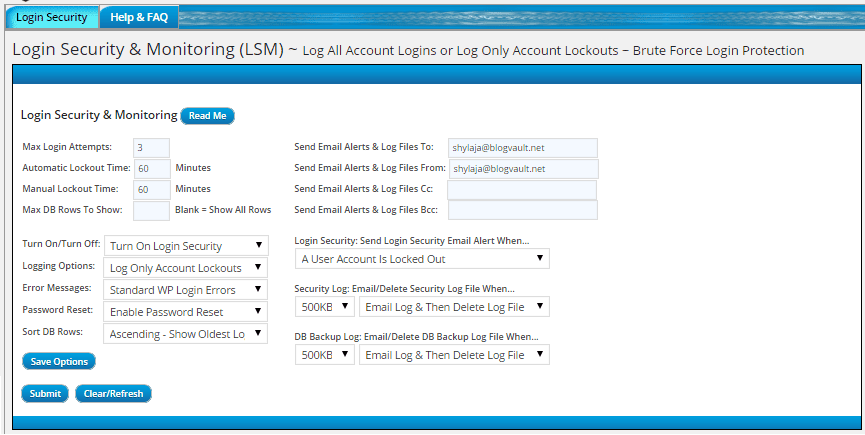
Another very useful way to protect your site against brute force attacks is by limiting the number of failed login attempts. This feature blocks out users once they reach the pre-configured number of failed attempts, for example 3. As bots tends to bombard our sites with indefinite login attempts, this mechanism is very effective in limiting their attempts.
There are many security plugins that help you limit the maximum number of failed login attempts. Such users are then blocked for a specified time period. There are plugins like Limit Login Attempts that are meant exclusively for this purpose. Other popular security plugins like BulletProof Security, All In One WP Security, Wordfence Security, iThemes Security, etc also help you with login security.
All security plugins enable mail notifications by default for failed login attempts or locking out a user. Considering the number of attacks on WordPress sites, admin accounts get bombarded with these emails every day. Apart from causing unnecessary panic, it is nearly impossible to sort through them. Even if you did, there is no specific action that you need to take. Hence we think it’s best to disable these notifications altogether or enable them only for specific events.
Additional Security Measures
We already learnt about the best practices to prevent brute force attacks. Here are a few more measures that are often used by WordPress users and their associated challenges.
Hiding the Login Page
As brute force attacks are dependent on presets, hiding the well known login page (wp-login.php) is strongly recommended as a security measure. This is the same page that you’re redirected to when you try to log into your site’s dashboard. Once the attacker lands on this page, he can launch an attack to crack your admin username and password. By renaming the login page to something else, you can add a layer of defense to your WordPress site.
We haven’t listed this measure in our top recommendations as we believe it has limited benefits. For one, the 404 error page that is displayed when someones tries to access the default login page doesn’t help in a big way. Server resources are still utilized in order to fetch and display this error page. So the bots can continue to attack your site and use up your resources. Moreover, this makes usability much harder as users normally expect the wp-login.php to be the access point when they want to make modifications to the site.
Managing IPs using htaccess
Htaccess files are configuration files that are present on your web server. They are used to control access to a specific directory. Since access control forms an important part in securing sensitive parts of your WordPress site, it can be very effective in preventing brute force attacks. You can use your htaccess file to ban specific IP addresses that shows up as a suspect in your logs. This is also known as blacklisting. Here’s how –
order allow, deny
deny from 192.168.20.10
allow from all
This logic can be extended to a range of addresses too.
order allow, deny
deny from 192.168.
allow from all
You can also manage access to your site by means of whitelisting. Permit only a set of known addresses and deny everyone else. This is nearly impossible to implement unless you are completely sure of your user network and hence won’t work with most sites.
order allow, deny
allow from 192.168.22.
deny from all
There are many challenges with using htaccess for access management. It requires a thorough understanding of IP addresses, networks, and rules which is beyond the comprehension of an average user. A small typo in a rule can result in a breakage. Moreover, you need to cleanup your htaccess file frequently. If left unattended, this can bloat up to a very large size and thus become unmanageable over time.
Two Factor Authentication
You might have used two-factor authentication with your gmail. The same has now been extended to WordPress too. In this method, another factor known only to the user is used along with username/ password for authentication. Almost all sites that implement this today use smart phones to send the one-time passwords (OTP). This is pretty effective because everyone has a phone within reach. Moreover, you can’t write down these passwords for later use unlike regular ones and thus reduced the risk of passwords being stolen.
Adding CAPTCHA
Adding CAPTCHA to your login form can prove quite useful in mitigating attacks. You can use a plugin like Captcha to do this. The CAPTCHA must be entered correctly along with the username and password in order to gain access. Therefore, even if the login URL is known, the default “admin” username is used, and a dictionary-based (i.e. weak) password is in effect, the odds of a successful brute force attack reduces significantly. The only problem with captchas is that they are sometimes be very hard to read.
Monitoring Failed Logins
One of our favorite plugins related to security, WP Security Audit Log, keeps a track of all the failed login attempts on your site. It lets you identify the users that are under attack, and can even email you in such situations. You can learn more about this feature here.
Conclusion
It is extremely difficult to put a complete stop to brute force attacks. But with multiple countermeasures like limiting login attempts and changing the default admin username, you can limit your exposure to these attacks. However, the best defense is to configure strong, impenetrable passwords. Act now, if you haven’t done so already.
Tags:
Share it:
You may also like
How to Limit Form Submissions with Droip in WordPress
Forms are an indispensable part of any website because of their versatility, letting you collect information for various purposes! However, people with ill intentions often attempt to exploit these forms…
How To Manage Multiple WordPress sites
Management tools help agencies become well-oiled machines. Each task is completed with the least amount of effort and highest rate of accuracy. For people managing multiple WordPress sites, the daily…

PHP 8.3 Support Added to Staging Feature
We’ve introduced PHP version 8.3 to our staging sites. Test out new features, code changes, and updates on the latest PHP version without affecting your live website. Update PHP confidently…
How do you update and backup your website?
Creating Backup and Updating website can be time consuming and error-prone. BlogVault will save you hours everyday while providing you complete peace of mind.

Updating Everything Manually?
But it’s too time consuming, complicated and stops you from achieving your full potential. You don’t want to put your business at risk with inefficient management.

Backup Your WordPress Site
Install the plugin on your website, let it sync and you’re done. Get automated, scheduled backups for your critical site data, and make sure your website never experiences downtime again.